Here are Alan Nouri's slides on Web Security
And here are his files.
README.txt
exploit.html
vulnerable.php
square.php
stafflogin.php
example_error.php
http://www.php.net/manual/en/
http://www.owasp.org/
http://www.regexlib.com/
http://www.sitepoint.com/
http://www.linuxjournal.com/article/7237/
Application Frameworks / Design Patterns
http://www.phpmvc.net
http://phrame.sourceforge.net
Most serious security breaches are not done by people breaking
codes or otherwise using high tech methods to find security holes;
they are done by low tech methods like looking over someone's shoulder
as they type their password. In fact many security breaches are
inside jobs in which people who have access to information steal or
modify it.
Everything in this class is based on the assumption that passwords
and keys are secure, and this is not a valid assumption.
Cryptography
There are two basic categories of cryptography systems
For many years the standard symmetric key system was DES. This is a block cipher. The key is 56 bits. The message is divided into 64 bit blocks, and then goes through a series of operations in which bits are permutated and then modified by portions of the key. This has the following strengths
When DES was first adopted as a standard in 1977, it not feasible
to try to break it with brute force, but today, it is difficult, but
not impossible, so newer ciphers have been developed. These are
also block ciphers, but they have a larger key. These include:
triple DES in which the message is encrypted three times
using DES, with three different keys. Since there 2168
possible keys, this is completely unbreakable, but takes three times
as long to encrypt and decrypt.
Advanced Encryption Standard (AES) a block cipher based
on a 128 bit block which supports
key sizes of 128, 192 and 256 bits.
Blowfish fast, compact, simple, with a choice of key sizes as high
as 448 bits based on a 64 bit block.
Here is a good overview of Block Ciphers
The problem with Symmetric key ciphers is key distribution. Two strangers who want to communicate securely have no simple way to agree on a key without an eavesdropper being able to read it.
The best known and most widely used public private key system is the RSA algorithm. Here is a link to a web site on the Mathematical guts of RSA
Wikipedia has remarkably good high level overviews of many such technologies. Here is their material on RSA
Public private key systems solve the problem of key distribution. If two strangers want to communicate securely, they simply exchange public keys. An eavesdropper can read the public keys, and can even encrypt messages to either party, but cannot decrypt the messages.
Public-private key ciphers are not more secure than DES (security depends on key size), and they will not drive out symmetric key encryption because it is much more computationally intensive.
The last two do not involve bad guys, but reflect a lack of trust between the sender and the receiver
Example: Alice buys 100 shares of ABC stock through an on-line broker, and shortly afterwards, the stock of ABC tanks. Alice then denies sending the buy order.
Example: Alice places a $100 bet with her on-line bookie on Bluenote in the Fourth race at Aquaduct. Bluenote wins the race and pays 10 to 1. The bookie denies receiving Alice's bet.
The answer depends on what kinds of threats you are concerned about. If all that you care about is non-disclosure (the bad guy cannot read your messages), then encryption can be part of the application level. However, security systems can potentially be placed at any layer in the protocol stack.
At the transport layer, there is Secure Socket Layer (SSL) and its close relative Transport Layer Security (TLS). SSL is used to encrypt and authenticate traffic between HTTP clients and servers.
At the IP layer, there is a complex set of standards called IPSec. The most common use of these is to support Virtual Private Networks (VPNs). In one form, the entire message, including the IP header, the TCP header, and the message itself, are encrypted, and a new IP header is stuck on the front of the message. Thus, an individual can communicate with a network which is behind a firewall. The firewall decrypts the message and passes it on to its destination. The bad guy, presumably outside the firewall (read the note at the top of the page), can see that someone is sending a packet to the firewall, but cannot learn the destination within the firewall, the port number, etc. This is called IP tunneling
It is theoretically possible to encrypt and decrypt message at the individual link level (i.e. between individual hops), but this is seldom done.
Authentication functions
The purpose of authentication is to prevent masquerade. When Bob receives a message which is supposed to be from Alice, how does he know that it was really sent by Alice and not someone pretending to be Alice.
If Alice and Bob have agreed on a private symmetric key. known only to the two of them, and Bob uses this key to decrypt the message, and the message seems to be English, this is reasonably good evidence that the message came from Alice. However, if that is not good enough, Alice can attach a Message Authentication Code (MAC) or a hash function to the message.
A Message authentication code is a public function of the message and a secret key that produces a fixed length value that serves as the authenticator (aka a cryptographic checksum)
MAC = Ck(M)
where M is the message, k is the key, and MAC is the fixed length value. These have the feature that it is impossible to derive the message from the MAC. A widely used MAC is the Data Authentication Algorithm (DAA), based on DES.
Hash function a public function that maps a message of any length to a fixed length hash value that serves as the authenticator. It does not use a key, so anyone can compute it
One widely used hash function is MD5 (message digest algorithm) which produces a 128 bit value Another is the Secure Hash Algorithm SHA-1 and its variants.
Here is a method of addressing masquerading, message modification, and source repudiation. It uses public-private encryption, symmetric key encryption, and a hash function. Alice wants to send a message to Bob.
When two strangers communicate over the Internet, how can each side be convinced that the other side is who they say they are.
X.509 is a widely used standard for digital certificates. It defines a framework for the provision of authentication services by the X.500 directory and its users. The directory may serve as a repository of public-key certificates.Each certificate contains the public key of a user and is signed by the private key of a trusted certifying authority (CA).
The structure of a X.509 v3 digital certificate is as follows:
* Certificate
o Version
o Serial Number
o Algorithm ID
o Issuer (ie the CA)
o Validity
+ Not Before
+ Not After
o Subject (the name of the cert owner, holder of the private key)
o Subject Public Key Info
+ Public Key Algorithm
+ Subject Public Key
* Certificate Signature Algorithm
* Certificate Signature (Signature of the CA, a hash code of
the other fields encrypted with the CA's private key)
Here is a link to the verisign web page. They are the largest issuer of digital certificates.
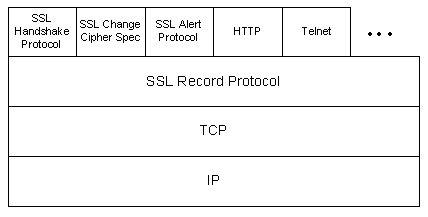
Secure Socket Layer (SSL) Originated by Netscape, SSL is used for secure client server communication over the internet. Provides confidentiality, authentication, and message integrity
SSL Architecture:

The Wikipedia SSL page provides a high level overview of how SSL works.
This link describes SSL better than I can Read it.
Here is a tutorial on the SSL handshake
Here is the class material on IPsec
and here is the Wikipedia on IPsec (it's not very good)
The major use of IPsec is to implement Virtual Private Networks (VPNs). Here is the FreeBSD page on VPNs and IPSec.
A conscientious student sent me his notes on this class in pdf form. Here they are.