Here is the Power Point Presentation on Cold Fusion
Here are the notes on BGP attacks
IPSec and SSL use the Diffie Hillman key exchange algorithm. This is a method which allows two strangers to agree on an encryption key without either party actually sending the key over the network.
Here is how the Diffie Hillman algorithm works
Note that both Bob and Alice know the key K, but Eve cannot calculate it even if she is able to intercept all of the messages.
However, the Diffie Hillman algorithm is subject to the man in the middle attack, so IPSec uses a variant called Oakley, which incorporates authentication and other security measures in addition to Diffie Hillman.
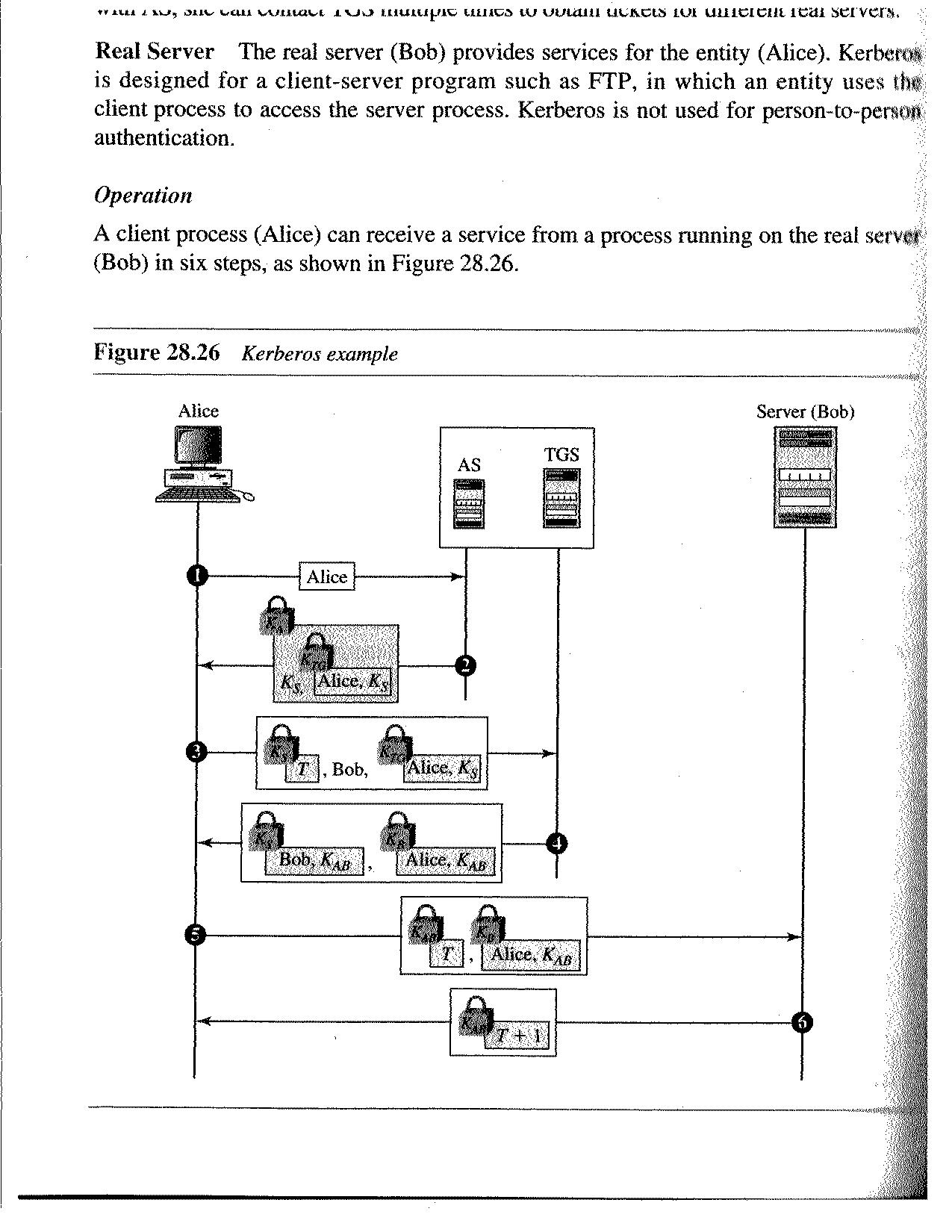
Kerberos
Developed at MIT as part of Project Athena in the 1980s. Very widely used now. It uses a different approach to security and authentication than other methods that we have seen.
Assume that we have a network of clients and servers. Assume that Eve can read every message sent, and can spoof any client or any server. We want to accomplish three things.
Here is how it works

and here is the explanation

Here is the program to compute RSA
And here are some notes on the RSA presentation taken by a thoughtful student